Technology Implementation for Higher Education in Prison
A Student-Centered Playbook for Planning, Preparing, and Assessing Implementation Readiness
-
Table of Contents
- Introduction
- Before You Think About Implementing New Technology
- Part I: Gauging Where You Are, Considering Where You Want to Get
- Sample Tools: Educational Outcomes and Technological Interventions
- Sample Tool: Technology Needs Diagnostic
- Sample Tool: Technology Risk Diagnostic
- Tool Templates: Gauging Where You Are, Considering Where You Want to Get
- Tool Template: Technology Needs Diagnostic
- Tool Template: Technology Risk Diagnostic
- Exercise: Mapping Stakeholders and Planning Collaboration
- Part II: Seeking Educational Technology to Improve Student Outcomes
- Phase One: Exploration and Planning
- Phase Two: Acquisition, Assessment Planning, and Milestone Marking
- Lessons From These Examples
- Phase Three: Preparation, Training, Pilot, and Beyond
- Conclusion: This is Only a Beginning
- Appendix: Relevant Resources
- Acknowledgements
- Endnotes
- Introduction
- Before You Think About Implementing New Technology
- Part I: Gauging Where You Are, Considering Where You Want to Get
- Sample Tools: Educational Outcomes and Technological Interventions
- Sample Tool: Technology Needs Diagnostic
- Sample Tool: Technology Risk Diagnostic
- Tool Templates: Gauging Where You Are, Considering Where You Want to Get
- Tool Template: Technology Needs Diagnostic
- Tool Template: Technology Risk Diagnostic
- Exercise: Mapping Stakeholders and Planning Collaboration
- Part II: Seeking Educational Technology to Improve Student Outcomes
- Phase One: Exploration and Planning
- Phase Two: Acquisition, Assessment Planning, and Milestone Marking
- Lessons From These Examples
- Phase Three: Preparation, Training, Pilot, and Beyond
- Conclusion: This is Only a Beginning
- Appendix: Relevant Resources
- Acknowledgements
- Endnotes
Introduction
Increasing access to and proficiency with technology has been identified as a core issue in both student basic needs and reentry and reintegration services.[1] However, a complex array of issues and constraints limit what technology is available to students who are incarcerated and how robustly they are able to access and utilize technology for educational purposes. With funding from Ascendium Education Group, Ithaka S+R has spent several years working to better understand what technology is available to college students in prison, how technology access and use are enabled or limited in a given setting, and what combinations of technology access and use might best prepare students for successful reintegration in the community and transition to college campuses outside prison.
As both the owner and operator of correctional facilities and the official oversight entity for higher education in prison programming, it is up to departments of correction to determine what technology to make available for education on the inside. This means that correctional leaders are responsible for considering the best interests of students from both the perspective of security and safety and the perspective of educational best practices. There is little research on how to negotiate these, at times differing, value sets. As a result, there are very few resources designed to help correctional leaders determine what technologies are available, how they might benefit students in their facilities, and what drawbacks the new technology might pose.
This playbook emerged from a pressing need identified by Ascendium Education Group for decision-making tools and frameworks to assist correctional leadership in navigating the complex landscape of educational technology for education in prison.
Building on lessons learned throughout nearly two and a half years of research on the changing role of technology in education in prison, we set out to understand student experiences of and perspectives on the use of educational technology in correctional settings. With help from our colleagues in JSTOR Labs, we then mapped out technology use in the student journey from secondary education through postsecondary education, considering how technology did or did not support learning needs, goals, and outcomes over the arc of their student careers. To accomplish this, we interviewed people who attended college in prison while incarcerated and asked them targeted questions about what education they received inside, the technology used to deliver or supplement it, and the training received to use it. With these student experiences grounding our exploration, we then studied how technology integrations in education in prison move from idea to implementation. We wanted to understand the process of acquiring, implementing, assessing, and sustaining technology for education in prison from the perspective of correctional leadership, with special attention to unexpected challenges, barriers, and gaps. Several current and former leaders in the field of correctional education participated in a design jam to discuss the field at large on video calls and took part in semi-structured interviews to understand how they have or are currently acquiring and implementing new technologies for educational purposes inside.
The tools and process outlined here are designed specifically to help correctional leaders center student outcomes and needs as they navigate the complex landscape of educational technology. However, we believe this playbook will also be of value to students, instructors, and administrators of higher education in prison in their self-assessment of and advocacy for educational technology, as well as to better understand, the challenges correctional leaders face.
Key Takeaways
- Quality access to and use of digital technologies for higher education in prison is both possible and necessary. A combination of changes in policy, practice, and funding are putting education technology within reach for higher education in prison, while a growing body of research suggests it is essential to educational equity and reentry success.
- Student experiences and student equity must remain centered throughout the technology planning, acquisition, and implementation process. Inequities may arise if student voices, educational experiences, and needs are not foregrounded: center them early, return to them often, and consider them in dialogue with security.
- Beginning with educational goals can help determine what technology will best serve those goals. The landscape of platforms, products, and providers can be overwhelming; simplify by working with college providers to identify key goals for and functions of technology.
- Implementation, maintenance, and upgrades are long-term, ongoing processes. Determine measurable outcomes and use them to assess the effectiveness of educational technology. Understand that integrating education technology in prison is an iterative process and that technology must be maintained, updated, and upgraded regularly to ensure its effectiveness.
- Collaboration and buy-in are key. Bringing stakeholders in early allows you to lean on the knowledge and expertise of others, improves coordination, and helps gain buy-in and trust.
The Playbook Process At-A-Glance
- Start by centering the student experience.
- Before you begin to think about technology, consider what concrete educational objectives and/or outcomes you are trying to improve or achieve.
- Ask what technologies can support that.
- Investigate your options alongside key stakeholders and ensure that they are engaged throughout the process.
- Explore how technology might intersect with existing policy and procedure.
- Ensure that policies and procedures governing technology use do not shutdown or shutter education for many if there are transgressions by few.
- Provide training to all relevant stakeholders and ensure that boots-on-the-ground staff from both corrections and education understand the importance of educational technology and
- Gather ethical data about usage and effectiveness from the start, so you can track them over time. Make sure this gathering complies with relevant correctional and educational policy.
- Reassess your objectives and outcomes regularly and ensure that technology is serving as a means to educational and rehabilitative ends.
Before You Think About Implementing New Technology
Center the Student Experience
The regulations governing the re-introduction of federal Pell grants for learners who are incarcerated note that oversight entities will now be required to consider whether a postsecondary education program operating in a prison provides academic services to students inside that are comparable to similar services provided to students on main college campuses outside.[2] This aspect of the regulations highlights the need to foreground student experiences and outcomes. Alongside these new reporting requirements for higher education in prison programs in federal Pell grant regulations, this is pushing the field toward a data-driven, student-centered approach to assessing college in prison.
With that context as backdrop, we are creating this playbook to help leaders in the field gain tools and strategies to explore how digital technologies intersect with questions of educational equity. This is part of a broader effort to shift research and assessment conversations away from a binary focus on only the access to technology or its absence. For example, rather than asking “can students use laptops?” we recommend pursuing a more nuanced exploration of how students experience technology access and use. So instead of asking a general question about policy, we might ask a series of more pointed questions about practice: How can students access laptop computers, for how often and for how long, in what environment, under what conditions, with what constraints or limitations? These types of questions allow us to examine differentiated student experiences.
We also want to keep the student journey through different educational milestones and systems in mind, i.e., the transition from high school or GED education to college. We know that there are often abrupt changes in educational technology and pedagogy across these divides, and very little training currently addresses these gaps. Consider how these transitions might impact student success, digital literacy, or reentry readiness, and plan to increase the seamlessness of the educational journey over time.
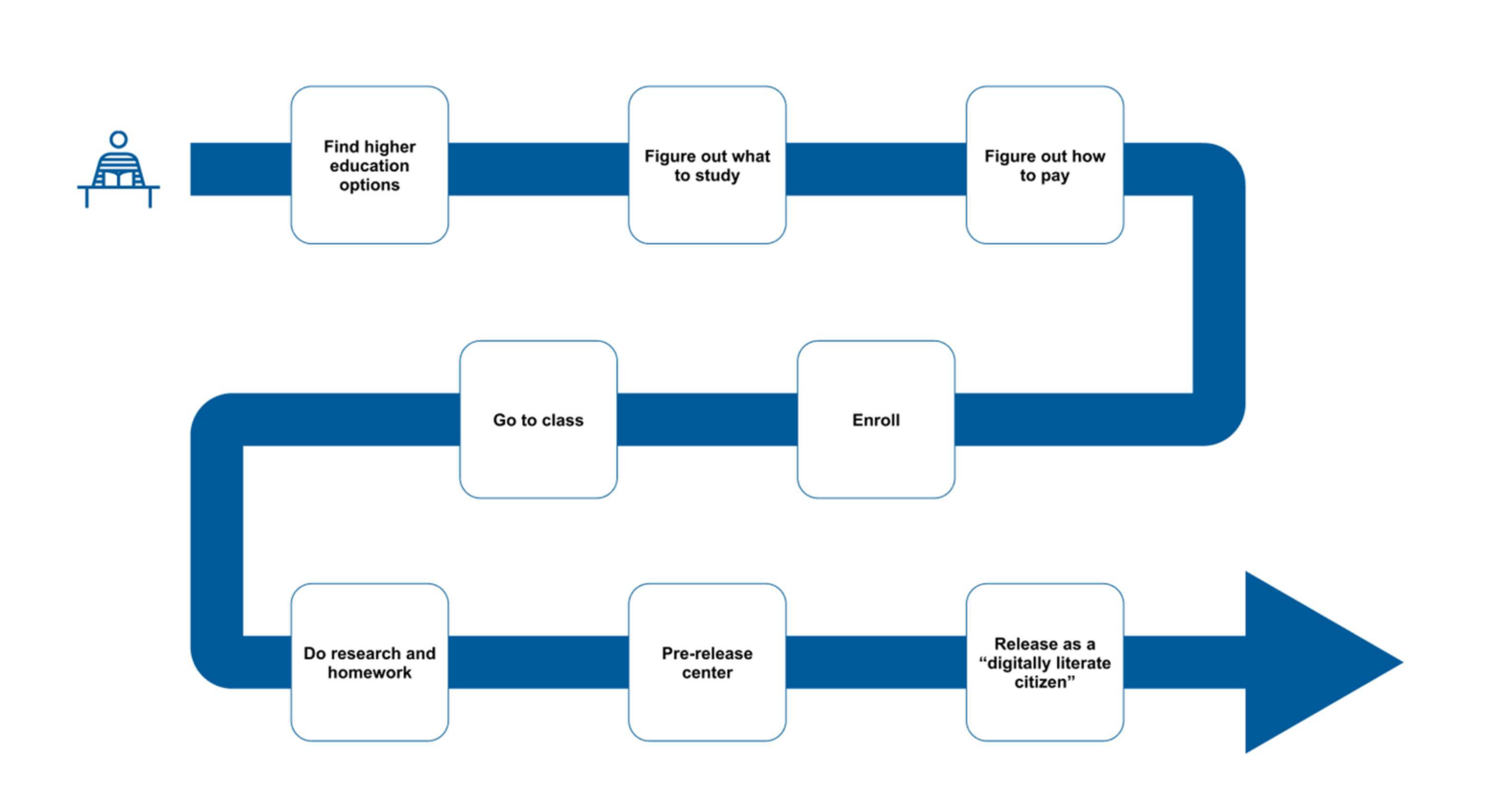 |
| Note: This map of the student educational journey is intended as a visual aid to help leaders contemplate how technology and information may factor into key moments in the student educational journey. Students in higher education in prison programs may not necessarily experience a linear or smooth progression, as this visual may imply. Not all students will experience all of the nodes included. Graphic by Nechelle Calhoun, Grace Cope, and Jessica Pokharel |
Prepare for Known Issues
Our research and conversations in the field have highlighted a number of recurring issues. While many of these will be addressed in more detail within the playbook, we feel they are worth naming up front.
- Cross-agency and cross-institution communication, coordination, and collaboration. Successfully obtaining, implementing, and maintaining new educational technology requires a tremendous amount of coordination and collaboration. Experts we spoke to in the field highlighted the importance of getting buy-in and feedback early from all relevant stakeholders.
- Policy constraints. Higher education in prison is governed by several overlapping sets of laws and policies—including at the state, correctional agency, facility, and educational institution level. These may constrain what technologies can be acquired, who must own and/or maintain them, and how they can be deployed.
- Financial and budgetary constraints. Procurement and service provision themselves may be costly, but it is also necessary to budget for long-term maintenance, updates, training, and personnel.
- Physical and architectural constraints. While providing students with long-term laptops with approved-listed Wi-Fi access for use throughout the facility might seem like an ideal best practice, structural and procedural limitations regarding electric infrastructure and the transmission of Wi-Fi signals, for example, make this impractical or even impossible in some locations. Another reason to collaborate and communicate early.
- Cultural barriers. Ensuring that correctional officers, IT personnel, educators, and administrators from both corrections and colleges support educational equity and the role of technology in it will be crucial to successful implementation and assessment.
- Negotiating the balance between security concerns and educational goals. Understanding and aligning across stakeholders on the goals for and limitations to introducing new educational technology is key to troubleshooting. Unforeseen issues are inevitable, so it is important to establish structures and procedures to address them without simply rolling back or removing technology.
Some of the leaders we spoke to emphasized how important and helpful it is to interact with peers working in other states and one highlighted the value of participating in a more targeted community of practice. Know that you do not have to do this work in isolation, and you do not have to create everything from scratch. You can find relevant resources on the website for the Resource Community for Higher Education in Prison (RCHEP), and individuals at research organizations like Ithaka S+R, and our colleagues at AIR, Jobs for the Future, RTI, and Vera Institute for Justice are here to help.
Consider the Benefits and Drawbacks of Purchasing Vendor Services Versus Developing Internal Structures
Leaders in the field offered nuanced positions and addressed just how long term and complex the process is to acquire, install, track, and maintain a new suite of technology, and states are taking different approaches. For example, California is building its own technology infrastructures from scratch, Wisconsin has established a patchwork arrangement with higher education institutions to help provide and develop their technology ecosystem for college in prison, and Michigan has turned to an external vendor to build, secure, maintain, and monitor their technology ecosystem. Correctional leaders who contracted with a full-service vendor highlighted the ease of the endeavor and were particularly excited that full-service vendors would negotiate subcontracting with additional application and content providers. The benefit, in their eyes, is in the time and headaches saved coordinating with additional vendors and service providers, as well as the internal labor saved by having the vendor secure and monitor devices and networks. Other correctional leaders, however, suggested that there is a downside to working with vendors: you become locked into long-term technological arrangements and relinquish agency and control to the vendor and reduce your own ability to experiment, pilot, or iterate. Know that there are vendors who provide individual services—such as access to academic databases or learning management systems—and full-service vendors who provide infrastructure, networks, devices, and monitoring services, and consider your own situation carefully.
Part I: Gauging Where You Are, Considering Where You Want to Get
Assessing Your Current Situation
The complex set of systems that must interact and coordinate to offer college in prison means that this education will, by necessity, look different in different places. If the goal is to offer high quality education inside that is comparable to postsecondary education outside of prison, then any assessment must begin with students. One place to start is with an exploration of student perceptions, opportunities, retention, and success. If you don’t already capture information about these topics, or if you are just beginning to offer or revise a college in prison program, this is a good time to set objectives and consider what data you will need to collect.
And, if you have not already established ways to do so, this may be a good time to consider how you will collect feedback directly from students. This can take the form of written evaluations or surveys, focus groups, and/or conversations with a representative student committee. The goal here should remain exploratory: we are not seeking to confirm a particular perspective or approach, but to understand how students experience the education program, what changes might improve that experience, and how it compares to, and prepares students for, college on the outside.
Regardless of how you collect data—surveys, interviews, focus groups—you should gather some information about how, when, where, and under what conditions students access technology for educational purposes. Researchers at Ithaka S+R and RTI have called these hidden conditions the dimensions of “quality of access” and “quality of use.”[3] These questions can help you identify hidden barriers to educational opportunity and equity.
After you’ve reflected on the student experience, it is a good time to consider what technology your education programs have at their disposal and what types of technology might increase access to education or improve student success, skills acquisition, and other outcomes.
Tip: Keep Accessibility and Accommodations in Mind
Legally, the department of corrections and the college or university partners they work with are both responsible for ensuring that students in higher education programs who have disabilities have equitable access to educational offerings and coursework. If you incorporate new technologies, work with your ADA coordinator, the college program, and their campus office for students with disabilities to ensure that the technology—and the way that it is being utilized by instructors and students—is accessible. It might be tempting to assume that accessibility has been achieved if accessibility features have been turned on in a device or courses have been developed with a universal design for learning approach; however, that may not necessarily be the case. Work with your ADA coordinator and the college program to create feedback pathways and to provide reasonable accommodations.
Tip: Think About Access to Technology Dynamically and Consider Quality of Access and Quality of Use
Our research on technology and higher education in prisons has made it clear that there are major barriers between how students can use technology in theory and according to formal policy, and how they can access and use it in practice. As you assess your current technology frameworks and think about how you might implement new technologies, track and consider what unexpected or material issues affect how, when, where, under what conditions, for what purposes, and for how long students can actually use technology for educational purposes.
Consider a couple hypothetical scenarios now. We’ll ask you to think about barriers to quality access and quality use later.
- Policy states that students have access to open computer labs in their residential unit where they can research, write papers, and read course materials in the morning, evening, and on weekends. In practice, though, the computer lab may only be open if there are adequate personnel to staff it, and the facility has been short-staffed on weekends since the COVID pandemic began.
- This would be a hidden barrier that limited students’ quality of access.
- Students can rent Chromebooks in a study hall space for up to four hours at a time to do their coursework; however, the study hall space is a mixed-use, multipurpose room, and it is frequently loud, hot, and overcrowded.
- This is an example of a situation that might impact the quality of use, as environmental conditions such as these are known to negatively impact student performance.
Sample Tools: Educational Outcomes and Technological Interventions
Below, we offer several brief sample self-assessments to help you begin to think through these processes. First, we offer each tool in-context and with sample answers. At the end of the section, you will find each of the tools as blank templates that you can print or use. Additionally, we are publishing the blank tool templates separately for use as a personal workbook.
The answers populated in these forms are entirely speculative and fictional; however, they may provide helpful examples of how to approach the material.
These assessments are designed to help you reflect, set intentions, and understand what constraints you might be facing and what supports you may already have to build on. Later, we will return to the assessment process in conversation with more stakeholders to establish objectives with measurable outcomes that we can use for long-term benchmarking and evaluation. At this point, however, we first want to understand the context, the student experience, how we might be able to improve or expand higher education inside, and what technology might be available to help us.
Sample Tool: Student Experience Diagnostic
This sample diagnostic is designed to gather and collate reflections on information about student learning experiences and outcomes. Assessment tools like this one are designed to help you do three things:
- Define and state your goals or intentions.
- Reflect on available information about how well you are achieving or progressing toward those goals or intentions.
- Determine how you might improve performance based on that information.
New programs or programs that are centering student experiences for the first time may find that they do not already have robust data or measurable educational objectives. We hope reading through these exercises will help these programs begin to take steps to develop them.
The sample below is populated with examples based on our knowledge and research. They do not refer to any specific department, program, or institution and should not be read as recommendations.
| Program Goals |
|
| Program Objectives | [Tip: objectives should be specific, measurable, and finite]
|
| Student Perspectives: Barriers, Challenges, Requests |
|
| Student Perspectives: Values, Benefits |
|
| Reflections: Student Access, Opportunity, and Outcomes |
|
Sample Tool: Technology Needs Diagnostic
Incorporating technology in educational program offerings is not an end in itself. Rather, we should start by asking: what technology do we need in order to reach specific outcomes or objectives? We must ground our thinking about technology through the importance of student outcomes and experiences, educational access and opportunity, course and degree offerings, and educational attainment.
Put simply: educational technology is a means to deliver, moderate, or supplement instruction and coursework. Education and its impacts are the end.
Below, we’ve provided a sample version of our Technology Needs and Readiness Diagnostic. The blank template is available at the end of this section and in a separate publication.
You’re considering implementing new technology. What goal are you supporting and what objectives are you trying to achieve in adding this new technology?
Goal 1: We provide students with educational choice.
Goal 2: We create multiple routes to degrees and account for nontraditional employment and education experience.
Objective: We are hoping to use technology to expand course offerings. We know that we need to provide more courses so that students can pursue alternate academic pathways. Because we already offer certifications and career training in landscaping and irrigation, we want to provide complementary coursework in environmental science as part of our interdisciplinary major. We want to set students up with preliminary training and credits that will help them progress toward degrees in sustainability, environmental studies, or landscape architecture.
Ideally, how would technology help you reach the objective(s) above?
I see two ways that technology could help. First, I’d like to get something portable that would allow students to access research sources, take notes, write papers, and do course readings outside of the education unit. This would allow us to increase course offerings without adding additional study hall times or creating crowding situations.
Is there already technology in place that serves similar purposes or meets similar needs? If so, what can you learn from them?
Not quite. Our secondary education programming uses tablets with self-paced curricula and coursework, and students with maximum security designations and medical based movement restrictions can use them in their residential quarters, so we can probably see what lessons we have already learned about how to secure, distribute, and keep track of those devices. We need more robust software and the ability to type essays and papers.
Are there any other goals or objectives that you might want this technology to support later?
Long term, we want to continue expanding educational offerings, but we are running out of space, and we haven’t yet found a good way to provide equitable education offerings to students who have maximum security designations. We have also had a couple situations where students have left class for medical or mental health reasons and had difficulties making up or completing coursework. We’d like to be able to provide them avenues to complete coursework in a timely fashion.
What constraints or barriers limit what technology you can acquire and implement? What might get in the way?
Money is a constraint. I don’t have the budget to buy new technology, get IT to secure and incorporate it, train COs, educators, and students on it. I’ll need some external source or partner to help.
There may be some security concerns about how the devices can be used if they can access any wireless networks. I don’t know whether we need internet access and Wi-Fi, 5G, or if a local network with restricted Wi-Fi is enough. And if we do one now and decide we want to move to another later, I want to make sure that wouldn’t be a big problem or expense.
Who can you turn to for advice or help brainstorming workarounds or solutions to the constraints you identified above?
In terms of money, I think my colleague in a different state got federal funding through the Digital Equity Act to do something like this. I can email her and see what she suggests. And I can ask my commissioner, they said that education is a priority going forward.
My IT director will know whether we need Wi-Fi, 5G, local networks, wired options or docks.
Thinking about the answer above, who else do you think should be looped in or brought onboard early? What stakeholders will need to be onboard for this to succeed, not just happen?
In addition to the commissioner, definitely my counterparts in IT and Security and Operations, the system-wide ADA coordinator, the administrator for the college in prison program, and the Student Voices Committee. Eventually, we’ll also need to get security staff, IT staff, educators, and students onboard and trained.
Sample Tool: Technology Risk Diagnostic
This tool was created at the suggestion of an individual we spoke with who thought that it could be useful for correctional education leaders to have a baseline sense of what the culture, expectations, and capacity for taking risks with technology are among staff, collaborators, and stakeholders within their system and/or facilities.
Implementing new technology comes with a certain degree of cultural translation—understanding how much support you have from supervisors and colleagues and how prepared staff, educators, collaborators, and students are to engage new technology may impact your pilot and launch planning. Not taking this into consideration can lead to pitfalls later. We also recommend using the questionnaire as a diagnostic tool to help you complete the Mapping Stakeholders exercise, also provided in this section.
This questionnaire can be completed by stakeholders through a survey or brief interview, and it is intended to gauge how collaborators feel about the potential risks, needs, and benefits of incorporating educational technology. Upon completion, you can gather and quantify responses from relevant stakeholders and use cumulative question scores to gauge the group’s collective sentiment. As the individual scoring and/or administering these questionnaires, you will also gain insight about whether there are specific people or departments that will be particularly ready, or resistant, to bring in educational technology.
The questionnaire should be completed by all relevant stakeholders, including, for instance:
- correctional and college system and institution leaders
- correctional and college IT leadership and staff
- correctional security and operations leadership and staff
- higher education in prison program administrators, instructors, and students.
This questionnaire is intended as a starting point and should be adapted and modified as needed.
In the example below, we have completed the questionnaire and initial reflection, Additionally, we offer some framing about how you might understand a response like this one.
Sample Questionnaire
Directions: For each of the questions below, indicate whether you strongly disagree, disagree, feel neutral, agree, or strongly agree with the sentiment expressed.
I feel that incorporating educational technology for higher education programming…
1. would have more risks than rewards for us.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
2. is too expensive.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
3. will be difficult for us to monitor and secure.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
4. is a luxury, not a necessity.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
5. is something we will need to do in the future, but not yet.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
6. is something we need to do, or I am committed to doing, but for which we are not yet prepared and/or trained.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
7. is something we should do but need more staffing or funding to do.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
8. is necessary for digital literacy and reentry.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
9. is something we are ready for.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
Questionnaire Reflection:
Directions: Take a moment to read over and consider your responses. It is likely that you will feel that the questionnaire did not completely capture your perspective. Use the space below to describe your responses in greater detail. You might try to explain the who, what, where, how, and why of some of your answers. For example, if you indicated you “strongly agree” that incorporating educational technology is something that you or your team are actively exploring, take the space here to get into the details about who is working on it, what they are doing, how the process is going, and why it has been initiated.
My impression is that we aren’t ready for tech, we can’t afford tech, we don’t have the staff for tech, and quite frankly students don’t need tech. I think we make too big a deal out of technology and fancy tools, but education is about learning, ideas, and dialogue. Reentry education is also different from college. College students learn a discipline and a profession, reentry teaches people how to reintegrate into society. So, sure, there they need to learn to use a cell phone and email, but that’s not education.
Considering Stakeholder Responses
After you have polled relevant stakeholders, consider what you’ve learned through this exercise. Did any answers or perspectives surprise you? Explore positions across roles and departments and consider how you can best address collective concerns and best leverage collective strengths and shared perspectives. This will also help you identify salient issues across stakeholders that may need to be planned for or addressed. For example, if across departments the majority of stakeholders indicated that they strongly agree that integrating educational technology is too expensive, then aligning on funding and financially sustainable implementation models will be important.
Keep these perspectives in mind as you move forward with strategic planning, making sure to address individual and collective concerns and leverage individual and collective enthusiasm or shared beliefs. This should also help clarify the information needed to complete the Mapping Stakeholders and Planning Collaboration exercise below.
For example, if we consider the sample responses above, we will know that this respondent is going to be resistant to technology implementation, but we also have a sense of why. This particular individual is less concerned about the risks that technology poses and more philosophically and fiscally opposed to the need to incorporate technology for educational purposes.
Given this, we might demonstrate how education technology is essential for achieving student learning objectives. So, if we are prioritizing ensuring that education inside is equitable or comparable to education outside, we may emphasize how experientially and technically important digital technology is to access educational materials, perform research, write papers, and complete assignments, or how a learning management system can help students track course progress and see graded assignments, etc. If our student learning objectives are aimed at information literacy and digital mastery for reintegration purposes, on the other hand, we might show how sustained use of and practice with digital technology is important for navigating support services or achieving employment success.
Consider: How else might we proactively and productively respond to their concerns around necessity and cost? What might their hesitance along these axes help us to understand about our current situation?
Remember: Our goal in this process is not to convince everyone of a specific perspective or objective, but to find the space where logistical and security concerns and student learning goals and objectives can both be met.
Tool Templates: Gauging Where You Are, Considering Where You Want to Get
Tool Template: Student Experience Diagnostic
- Define and state your program goals and measurable objectives.
- Use information to reflect on how well your program is performing.
- Determine how you might improve performance and/or solve problems.
Remember:
- Make objectives specific, measurable, and time-limited so you can gauge performance.
- If you have little to add to the form, create objectives that will help you gather the information needed to assess programming more fully in the future.
| Program Goals |
|
| Program Objectives | [Tip: objectives should be specific, measurable, and finite]
|
| Student Perspectives: Barriers, Challenges, Requests |
|
| Student Perspectives: Values, Benefits |
|
| Reflections: Student Access, Opportunity, and Outcomes |
|
Tool Template: Technology Needs Diagnostic
Incorporating technology in educational program offerings is not an end in itself. Rather, we should start by asking: what technology do we need as a means to reach specific outcomes or objectives? We must ground our thinking about technology through the importance of student outcomes and experiences, educational access and opportunity, course and degree offerings, and educational attainment.
Put simply: educational technology is a means to deliver, moderate, or supplement instruction and coursework. Education and its impacts are the end. Use the questions below to help you clarify some of the specifics about how you want technology to function in order to meet specific objectives.
- You’re considering implementing new technology. What goal are you supporting and what objectives are you trying to achieve in adding this new technology?
- Ideally, how would technology help you reach the objective(s) above?
- Is there already technology in place that serves similar purposes or meets similar needs? If so, what can you learn from them?
- Are there any other goals or objectives that you might want this technology to support later?
- What constraints or barriers limit what technology you can acquire and implement? What might get in the way?
- Who can you turn to for advice or help brainstorming workarounds or solutions to the constraints you identified above?
- Thinking about the answer above, who else do you think should be looped in or brought onboard early? What stakeholders will need to be onboard for this to succeed, not just happen?
Tool Template: Technology Risk Diagnostic
This questionnaire can be completed by stakeholders as a survey or as a brief interview, and it is intended to gauge how collaborators feel about the potential risks, needs, and benefits of incorporating educational technology. Upon completion, you can gather and quantify responses from relevant stakeholders and use cumulative question scores to gauge the group’s collective sentiment. As the individual scoring and/or administering these questionnaires, you will also gain insight about whether there are specific individuals or departments that will be particularly ready, or resistant, to bring in educational technology.
The questionnaire should be completed by all relevant stakeholders, including, for example:
- correctional and college system and institution leaders
- correctional and college IT leadership and staff
- correctional security and operations leadership and staff
- higher education in prison program administrators, instructors, and students.
This questionnaire is intended as starting point or a template and should be adapted and modified as needed.
Directions: For each of the questions below, indicate whether you strongly disagree, disagree, feel neutral, agree, or strongly agree with the sentiment expressed.
Questionnaire
I feel that incorporating educational technology for higher education programming…
1. would have more risks than rewards for us.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
2. is too expensive.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
3. will be difficult for us to monitor and secure.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
4. is a luxury, not a necessity.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
5. is something we will need to do in the future, but not yet.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
6. is something we need to do, or I am committed to doing, but for which we are not yet prepared and/or trained.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
7. is something we should do but need more staffing or funding to do.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
8. is necessary for digital literacy and reentry.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
9. is something we are ready for.
(1) Strongly Disagree (2) Disagree (3) Neutral (4) Agree (5) Strongly agree.
Reflection: Take a moment to read over and consider your responses. It is likely that you will feel that the questionnaire did not completely capture your perspective. Use the space below to describe your responses in greater detail. You might try to explain the who, what, where, how, and why of some of your answers. For example, if you indicated you “strongly agree” that incorporating educational technology is something that you or your team are actively exploring, take the space here to get into the details about who is working on it, what they are doing, how the process is going, and why it has been initiated.
Considering Stakeholder Responses
After you have polled relevant stakeholders, consider what you’ve learned through this exercise. Did any answers or perspectives surprise you? Explore positions across roles and departments and consider how you can best address collective concerns and best leverage collective strengths and shared perspectives. This will also help you to identify salient issues across stakeholders that may need to be planned for or addressed. For example, if across departments the majority of stakeholders indicated that they strongly agree integrating educational technology is too expensive, then aligning on funding and financially sustainable implementation models will be important.
Keep these perspectives in mind as you move forward with strategic planning, making sure to address individual and collective concerns and leverage individual and collective enthusiasm or shared beliefs. This should also help clarify the information needed to complete the Mapping Stakeholders and Planning Collaboration exercise below.
Exercise: Mapping Stakeholders and Planning Collaboration
This exercise will help you take stock of all the people you will need to have onboard for education technology implementation to work. We recommend first simply answering the questions and then organizing your responses into a visual list.
Before you begin, what individuals, offices, or departments do you need onboard to…
- help you decide what educational objectives you want technology to address?
- learn and decide what technologies might help you reach those objectives? What different infrastructures you might create to use those technologies?
- learn about the different ways you might acquire, secure, monitor, and maintain those technologies?
- help you find the funding or budget to incorporate these technologies?
After you’ve decided on technology, what individuals, offices, or departments will you need on board to…
- acquire the technology?
- install the technology?
- implement the technology?
- ensure that the technology is broadly accessible?
- train stakeholders to understand what the technology is, why it is important, and how it will be used?
- train staff to ensure it is secure?
- develop and write policies on how, when, where, and under what conditions the technology may be used?
- develop and write procedural guidance on how to navigate questions when these policies conflict with other existing policies?
- develop and write procedural guidance on what to do if technology is misused, damaged, or abused?
After you’ve implemented the technology, what individuals, offices, or departments do you need on board to…
- make sure that the implementation is successful and the technology is supporting educational goals?
- gather stakeholder feedback on the process and outcomes?
- troubleshoot problems, errors, issues, or accidents?
- ensure that issues with accessibility and disability accommodations are received and addressed in timely fashion?
- update and maintain the technology and the trainings on how to use it?
- monitor usage data to understand the quality of access and quality of use?
- ensure that all data collected is gathered, stored, and shared in accordance with relevant DOC policies and procedures and the policies governing educational rights and privacy (i.e., FERPA)?
- tell compelling narratives about what you are accomplishing that will also drive your educational offerings where you need them to go?
Note: consider these responses alongside the previous ones to understand who might get on board easily, where you will need to build bridges, and where resistance might come from, or compromise might be necessary.
Part II: Seeking Educational Technology to Improve Student Outcomes
Phase One: Exploration and Planning
Now that you have examined where your programming is and planned the student learning outcomes that you will prioritize, it is time to begin considering what technology will be most helpful in achieving those objectives. This section provides high-level information about technology platforms. We also look at how other factors may have an impact on the quality of access to and use of different types of technology.
The landscape of educational technology is expansive and rapidly changing, and there is no one-size-fits-all solution to incorporating technology into higher education in prison programs. Instead of simply seeking the best technology, leaders in the field emphasized the importance of seeking the right technology, developing the right infrastructure, and drafting the right policies and procedures for their specific systems, facilities, and educational needs. We spoke with leaders who were responsible for securing civilian technology and building bespoke, secure networks and technology infrastructures from scratch. We also spoke with leaders who contracted with external vendors to build custom technology infrastructure, provide secure devices, and monitor and maintain network access remotely. Each decision maker that we interviewed emphasized that the choice they made was the right one in their state or for their system.
Leaders in states that developed technology infrastructure from the ground up and manually secured devices touted the level of customizability, repairability, upgradability, and control that this afforded them. They also extolled the virtues of ensuring that access to sensitive student data was properly limited and of not being locked into long-term contracts. Leaders in states that worked with vendors to install customized technology infrastructures and acquire secure devices suggested that having vendors work to subcontract with additional service providers—such as for certification and testing, educational software, and digital libraries or databases—made their lives easier and reduced decision fatigue.
Consider: Technological Devices
Currently, facilities use three types of technological devices to deliver or supplement college in prison programming: tablets, desktop computers, or laptops, Chromebooks, or digital notebook devices. Some correctional technology ecosystems already allow students robust, comparable access to industry standard technology for educational purposes, providing, as one example, laptops with wireless access to secure internet, cloud storage, and standard learning management systems. However, this type of arrangement might be out of immediate reach for a variety of reasons, including policy, culture, funding, staffing, infrastructure, and architecture. Moreover, attempts to purchase technology before determining the specific goals to support, objectives to reach, and milestones to celebrate and assess progress can lead to unexpected and costly challenges.
Our 2023 survey of technology access in higher education in prison programs indicated that some college in prison programs deploy multiple types of technology for educational purposes—for example, one program indicated that they allow students access to laptops or Chromebooks in educational facilities, a computer lab with open hours in their residence, and linked access to course readings and supplemental materials on a tablet. A technology ecosystem like this can deploy existing resources, such as a computer lab and tablets primarily used for entertainment purposes, in tandem with new resources like tablets to access course readings and research materials and multiple-hour loans of laptops for coursework, homework, and writing in a setting where access may be more limited. The point is not to provide the most technology, but to make sure that the technology you are deploying best (1) serves the needs of your students, (2) supports the outcomes you are trying to achieve, and (3) incorporates the resources you have available.
Below, we’ve included a visual tool to help you consider what kind of device or devices—tablets, laptops, or desktop computers—might be right for your situation. Remember that there is no one right answer and the best solution in the current moment might require creative, lateral thinking, for example using different technologies to meet different student needs in different educational contexts.
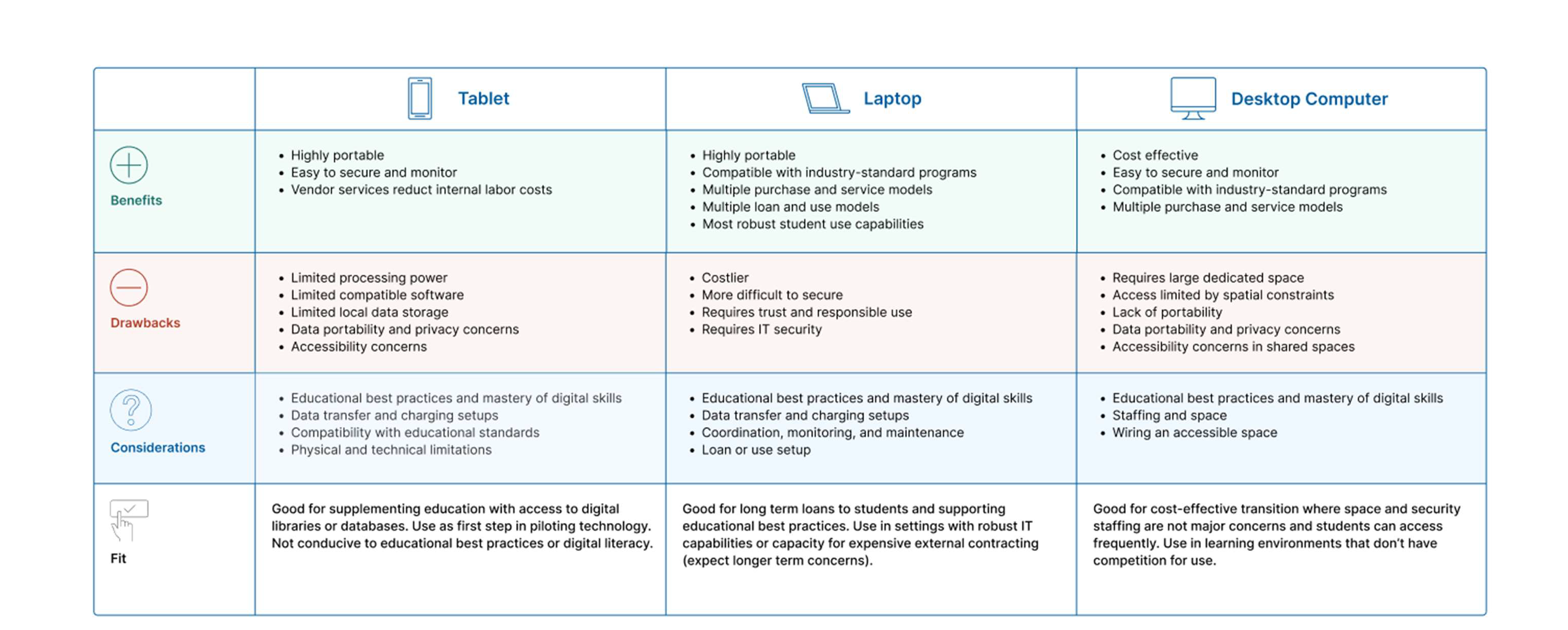 |
| Graphic by Nechelle Calhoun, Grace Cope, and Jessica Pokharel |
Considerations by Device Type
Understanding how different types of technological devices vary, and how they might be used for different purposes, can help you select the technology that best supports your students and intended outcomes, among what is possible in your given situation. Within each category above, devices also vary widely and are often customizable based on your logistical and educational needs—and the budget you have to work with. Instead of listing specific devices and their customizable options, which could quickly become overwhelming or outdated, we’ve provided two tables to help you understand at a glance the rough range of features available in secure tablets, and laptops, Chromebooks, or notebooks. Because we know that this list is based on limited information and the market is rapidly changing, we have also included some questions to consider.
Technology Menu: Secure Tablets
Accessibility features and ADA ComplianceMany providers are not actively ensuring that devices have functional, built-in accessibility features. Be sure to inquire about this.Some potential tools or services to inquire about: text to speech, voice/talk/speech to text, screen magnification, font size customization, audio control and output options, screen rotation preferences, sleep mode and unlock options, compatible with external tools/devices/software.
| Screen size | 7″ to 10.5″ | This is slightly larger than the average screen size of a cell phone, which is roughly 6.5 inches. So, assignments with visual components may be difficult to see properly and word processing may be more difficult. |
| Weight | 1.06 lbs to 2.25 lbs | |
| Keyboard | Integrated onscreen, Bluetooth compatible, wired | Keyboard size varies, but small keyboards and onscreen keyboards may pose accessibility concerns and make sustained typing impractical. |
| Battery life | 6-20 hours | Will vary by applications used, important to consider alongside connection type. |
| Battery connection and charging | Charging docks, charging carts, wireless (induction) charging, power adapter to outlet, power adapter to USB. | |
| Headset or earbud compatible | Earphone jack, Bluetooth compatible | |
| Camera | May or may not include built-in camera, if present front-facing for video calls | Some devices with front-facing cameras have facial detection or facial recognition technology, others automatically lock camera access outside of special applications. |
| Microphone | May be built-in or provided in headset | |
| Content storage | No local storage to 32 gigabytes | |
| Software, programs, databases | Vary widely and may include proprietary, open source, third-party, or all of the above. | Key questions to consider or ask: compatible with industry standard learning management systems, compatible with industry standard word processing software, design software, architecture software, engineering software, video and/or audio production software, access to scholarly databases and/or library resources, email or direct messaging to communicate directly with program staff/faculty/advisers |
| Network connection type | Wired (docking), wireless (cellular network – 3G, 4G, or 5G), Wi-Fi (local network or internet) | The quality of access and quality of use may be impacted by the way devices access information—and any charges there might be for uploading, downloading, or using applications. Be sure that the connectivity you are selecting meets your student needs, educational plan, and your resources available. Be aware that some wireless options may be difficult to access or install given geographical, architectural, or design limitations. |
Technology Menu: Secure Laptops, Chromebooks, Notebooks
| Screen size | 10.1″ to 13.5″ | May vary, can be larger for devices not already marketed as secure. |
| Weight | 1.1 lbs to 3.5 lbs | May vary, can be larger for devices not already marketed as secure. |
| Battery life | Very little info available, likely to vary based on variety of factors. | |
| Connection type | Charging carts, power adapter. | |
| Headset or earbud compatible | Wired, wireless | |
| Camera | May or may not include built-in camera | |
| Microphone | May or may not include built-in microphone or be headset compatible. | |
| Content storage | Will vary and is likely customizable from 32 gigabytes to 512 gigabytes | |
| Processing memory | Will vary and may be customizable. 8 gigabytes RAM will work for limited processing and multitasking, 16 gigabytes RAM or higher may be required for video production or specialized software. | |
| Accessibility features and ADA Compliance | Secure laptops, Chromebooks, and notebooks accessibility features will likely vary based on operating system (which may be customizable). It may be important to ask if accessibility features are functional when the device is not actively connected to a network or if other optional features are not enabled or activated. | Some potential tools or services to inquire about: text to speech, voice/talk/speech to text, screen magnification, font size customization, audio control and output options, screen rotation preferences, sleep mode and unlock options, compatible with external tools/devices/software. |
| Software, programs, databases | Vary widely and may include proprietary, open source, third-party, or all of the above. | Key questions to consider or ask: compatible with industry standard learning management systems, compatible with industry standard word processing software, design software, architecture software, engineering software, video and/or audio production software, access to scholarly databases and/or library resources, email or direct messaging to communicate directly with program staff/faculty/advisers |
| Network connection type | Wired (docking), wired (ethernet), wireless (cellular network – 3G, 4G, or 5G), Wi-Fi, other (e.g., wired coaxial) | The quality of access and quality of use may be impacted by the way devices access information—and any charges there might be for uploading, downloading, or using applications. Be sure that the connectivity you are selecting meets your student needs, educational plan, and your resources available. Be aware that some wireless options may be difficult to access or install given geographical, architectural, or design limitations. |
Consider: Technology Vendors, Service Providers, and Ground-Up Builds
The landscape of vendors and service providers actively offering technological devices, software, or other related services in correctional education settings is changing rapidly. The fact that different institutions of higher education might bring their own expectations, standards, policies, procedures, and contractual obligations into a facility adds to the complexity of establishing a technology framework.
There is a limited but growing number of full-service vendors who provide and install technological devices and software and programs, wireless or wired networks, IT support, technology maintenance, digital security, and technological monitoring. Various providers offer secure tablets, secure laptops, Chromebooks, or notebooks, or bespoke computer labs with desktops and/or laptops in a secure location. While full-service educational technology systems can be appealing, they come with a hefty price tag and may lock systems or institutions into long-term contracts that limit their ability to adapt, refine, or expand systems.
Legal Compliance
Contracting services to these vendors means that they will be in control of and responsible for critical student information and data, as well as for the proper functioning of systems, accessibility features or tools, and technologically reliant disability accommodations. This makes it crucial that departments of corrections, individual correctional institutions, education partners, and technology vendors are all aligned on, communicating clearly about, and coordinating to comply with the Family Education Rights and Privacy Act (FERPA), the Americans with Disabilities Act (ADA), and Section 504 of the Rehabilitation Act. In May 2024, the federal Department of Health and Human Services finalized a new rule to strengthen protections against disability discrimination that went into effect 60 days after publication, but agencies will have a two-year window to comply. It clarifies compliance requirements for government agencies and the organizations with which they contract under Section 504. If correctional or postsecondary education leaders are considering working with full-service vendors, they need to discuss how these vendors will meet the new, more stringent requirements.
Consider: Technology Infrastructure and Educational Ecosystem
Our interviewees emphasized that they want their students to have the same educational experience on the inside that students on the outside have every day. Additionally, they want students to learn and master the skills that will be crucial to their successful reentry and integration into the outside campus or the workforce. Finding a way to do this becomes something of a systems-level puzzle: how can you provide a secure learning management system, enable email and messaging, limit duplicative work for educational faculty, and provide a learning environment that reflects the technology and pedagogy students might encounter on campus outside of prison?
There is a spectrum of answers to these questions. At one extreme, a facility may rely on a full-service vendor and mandate that all educational partners uniformly adopt that technology. At the other, a facility may choose to build its own technology infrastructure from the ground up. Understandably, the majority of correctional leaders will find their own answers somewhere in the middle. Some may choose to combine vendor-provided devices and services for one type of activity—providing access to research databases through vendor-provided tablets—while offering desktop computer labs for coursework. Others may build their own internal networks but turn to service providers to offer secure internet and applications.
While the options can easily be overwhelming, understanding how different technologies and services fit together—or don’t mesh at all—can help to narrow your decision. For example, one interviewee noted that they could not use a full-service vendor to integrate existing resources—digital libraries, databases, and educational programming—onto new devices and networks because of technical and contractual limitations. They decided that such limitations made working with a full-service vendor the wrong choice for them.
Expanding technology infrastructure from the ground up is, however, no small feat. It requires skilled, experienced IT professionals, as well as internal and external coordination and collaboration. In addition, securing, maintaining, and sustaining a network will require retaining dedicated staff. The people we spoke to disagreed on the value proposition here: some leaders felt that vendors reduced logistical work to such an extent that it is worth it to pay large fees and let them deal with the details and the maintenance, while others intimated that it is more cost effective and sustainable to build systems internally. Either way, acquiring, installing, implementing, and maintaining new technology comes at a cost.
Tip: Finding Funding
How can you fund developing and expanding technology for educational purposes? There are a number of avenues available to secure funding for educational technology. Securing funding sources may require skilled proposal writing, cross-agency coordination and agreement, or support from the state legislature or governor’s office. Below, we’ve noted some sources where relevant funding is, or has recently been, available.
A note of caution: Vendors are also aware of these options, and some may offer to help you secure funding. Before agreeing to any such arrangement, make sure that the technology and services these vendors offer fit the needs of your students and the objectives you’re trying to achieve. A concise list of some of the sources available to fund education technology expansion and implementation are briefly sketched in the Appendix: Relevant Resources
Tip: Thinking Sustainably
As the structure of this playbook suggests, it is important to think about the long-term application and maintenance of technology systems. Technological devices and software can become dated at a moment’s notice.
As you plan to acquire and implement new technology for education in prison, consider also:
- How you will provide training for staff, instructors, and students.
- How the devices and network will be maintained, updated, and upgraded, by whom, and how this can be accomplished with minimal disruptions to quality access and quality use.
- What longer term plans you might have to expand offerings or access or integrate other technologies and services.
- What freedom or modularity you need to maintain to support those goals later, without needing to overhaul the infrastructure you are building.
Implementing new technology is not a one-time cost with one-time labor concerns, but rather something that will require dedicated funding, staffing or vendor support, and servicing over the lifetime of the technology and the network.
Exercise: Considering Constraints and Supports, Generating Solutions
This exercise is a modified version of one developed and practiced by our colleagues at JSTOR Labs and draws on design workshop principles.[4] While it can be a useful exercise for an individual to complete, it will serve you best if you do it collaboratively with the stakeholders identified in the “Mapping Stakeholders and Planning Collaborations” exercise above.
We recommend that you set aside two to three hours to complete all three phases of the exercise in a group, discuss and debrief, and plan next steps together.
Directions for facilitation and notetaking: this exercise works best when you gather stakeholders that have different expertise and perspectives and will serve different roles in the implementation process. We recommend that you also engage students and instructors who will be responsible for using the new technology within the education setting in this phase. With this diverse group of stakeholders, you can identify risks, barriers, and potential issues, and collaboratively plan and develop mitigations and solutions. A note of caution: make sure that you plan time to think through supports and iterate solutions, consider constraints, and provide equal time for each phase. This exercise can be targeted to specific phases of implementation and repeated as needed.
Begin by convening the group and explaining the general process, the specific activities, and the intended goals and outcomes of the session. Take breaks between the activities for five to 15 minutes.
Materials required: several pads of sticky notes, writing utensils, a surface and space where you can place and rearrange sticky notes. This exercise can be adapted for remote facilitation with the use of a virtual sticky note board that can be synchronously edited. (Software programs such as Mural or Miro provide this function.)
1. Setting Up the Activity
- Distribute sticky notes and writing utensils so that everyone has access to them.
- This activity works best if you use a second, different colored set of sticky notes, so that you can put solutions and supports next to constraints and barriers and see the difference. If you only have one color of sticky note, you can visually set supports and solutions to the side of constraints.
- Align on the goal or intention of the meeting in general and this exercise in particular.
- Remind everyone what your educational objectives are and how you hope [target technology] will help you achieve them.
- The first exercise will help you to identify constraints that limit how [target technology] might be acquired, installed, implemented, maintained, serviced, and updated or upgraded as necessary.
- Start with a series of open questions for the group to consider:
- What barriers or constraints are there to acquiring technology?
- How might policy, procedures, regulations, culture, staffing, logistics, funding, space, technology infrastructure, or other miscellaneous factors limit how, when, and where you can implement [target technology]?
- How might they limit who has access to it or how it can be used? What policies, procedures, protocols, and plans might you need to secure it?
- What policies, procedures, protocols, and plans might you need to ensure that students have enough quality access and use to achieve the educational objectives you’ve set?
- The goal is to consider everything that might limit how you can use [target technology] or be a barrier to successfully implementing it to achieve your stated educational objectives.
- Start by thinking about your role in particular and what obstacles you might identify from that perspective. Don’t stop yourself from writing other constraints you identify, though.
- Allow 10-15 minutes for people to write independently, ask them to keep each constraint or barrier to a single sticky note and to write as many as come to mind.
- Prepare to wind this phase down when people begin to slow down or stop writing.
- After time has expired or people have stopped writing, ask people to take a few minutes to reread what they wrote and consider:
- Are there themes or categories that stand out? For example, technical limitations due to infrastructure? Policy barriers? Procedures that might slow or stall implementation? Etc.
- Ask each person at the table to read out what they wrote on each sticky note and to place them on a surface where you can organize and rearrange them. Discuss with the group how you might categorize each sticky note as you add it.
- This might seem arbitrary, but the goal here is to visually cluster similar issues, since we will start to think of solutions soon. This series of activities also speaks to different learning styles (leveraging written, visual, verbal, aural, and tactile/kinesthetic components).
- To end the activity, offer provisional labels for each category or group of sticky notes.
- Announce a brief break and ask people to consider:
- What supports do you have to implement [target technology]?
- Thinking about the broad categories of barriers and constraints, are there solutions or strategies that you might use to get past or around these barriers?
- Thinking about specific constraints close to your role, what can you or your department or team do to support success or develop solutions?
3. Considering Supports and Generating Solutions
- Reconvene the group after your short break and ensure that there are ample sticky notes and pens.
- Building on the questions that you asked before the break we’re going to repeat the structure of the previous activity, but focus on supports, guardrails, and solutions that work within our constraints and get us around the barriers we’ve identified.
- The goal is to consider everything that might help you to successfully implement [target technology] and achieve your stated educational objectives.
- Start by thinking about your role in particular and what supports you might be able to identify, secure, or provide from that perspective. Don’t stop yourself from writing other supports or solutions you identify, though.
- Allow 10-15 minutes for people to write independently, ask them to keep each support or solution to a single sticky note and to write as many as come to mind.
- Remind participants to feel free to revisit the constraints and barriers you identified and to think of how to counter or prepare for them, in particular.
- Prepare to wind this phase down when people begin to slow down or stop writing.
- After time has expired or people have stopped writing, ask people to take a few minutes to reread what they wrote and consider:
- Do the supports and solutions identified fit in the same categories, cut across them, or exist outside them?
- Do they respond to specific constraints or barriers? To clusters or groups?
- Do you see themes or categories in the solutions and supports that you did not identify in the constraints?
- Ask each person at the table to read out what they wrote on each sticky note and to place them near the constraints or barriers they are associated with. Discuss what each solution or support might require with the group as they are placed.
- Provide another short break here to allow people to process the activity.
4. Creating a Collaborative Plan
- Begin by debriefing and discussing what the exercise revealed to the group.
- What surprised people?
- What constraints or barriers did someone else address that you might have missed?
- What supports or solutions did someone else suggest that you might not have come up with on your own? What solutions or supports could you not enact on your own?
- After this discussion come up with an outline of a plan and agree on a loose timeline for standing up your [target technology].
- As you develop your plan, consider first, a high-level overview of the process:
- What major phases will the process consist of?
- Some phases might include:
- Clarifying or prioritizing goals to support and student learning objectives to achieve
- Exploration
- Tools and technology available
- How they fit with existing technology, infrastructure, and what additional infrastructure and logistical needs they might alleviate or require
- Vendors that can deliver relevant products or services
- Peers who have implemented and stood up similar interventions
- Internal resources and/or appetite to build from scratch
- Tools and technology available
- Some phases might include:
- What major phases will the process consist of?
-
-
-
- Acquisition
- Who will be responsible for:
- Funding?
- Acquiring the new technology?
- Logistical coordination?
- Planning on how to incorporate technology with existing systems?
- Planning how to incorporate technology in the specific type of education?
- Who will be responsible for:
- Implementation
- Who will be responsible for:
- Installation?
- Testing, piloting, and implementation?
- Training?
- Establishing policies and procedures?
- Developing and authoring contracts, memoranda of understanding, and/or user agreements?
- Tip: make sure that you create student use agreements that establish policies and procedures to ensure that a breach or an abuse of technology does not disrupt or punish all potential users.
- Gathering data about how the technology is working and whether it is contributing toward targeted objectives?
- Who will be responsible for:
- Evaluation and Maintenance
- Who will be responsible for:
- Maintaining, updating, and upgrading technology?
- Benchmarking and evaluating data gathered to assess the value and effectiveness of the added technology?
- Establishing new or revised objectives based on benchmarks and evaluation?
- Assessing how technology, training, policies, procedures, staffing, or other factors might be adjusted to improve the quality of student access to or use of technology?
- Assessing how technology, training, policies, procedures, staffing, or other factors might be adjusted to improve the effectiveness of instructional use of the technology?
- Assessing how technology, training, policies, procedures, staffing, or other factors might be adjusted to improve the security considerations related to the technology?
- Who will be responsible for:
- Acquisition
-
-
Phase Two: Acquisition, Assessment Planning, and Milestone Marking
After you’ve identified the goals you’ll be supporting, the objectives you hope to achieve, the stakeholders or collaborators you’ll need to work with—and their respective roles in the process—it’s time to begin acquiring technology, planning what data to collect on how it is used and how effectively it is supporting targeted objectives, and what major milestones you will use to mark progress in your implementation plan.
Consider: Leveraging the Stakeholders and Experts at Hand
This process might seem overwhelming when it is laid out in bullet points or plotted in a calendar. Fortunately, you’ve already identified the stakeholders and collaborators you need for success. Your IT department, your security and operations team, your educational staff, and your students will all have valuable input and expertise on different aspects of the technology implementation process. Engage them throughout.
Your peers and colleagues in other systems have gone through or are going through this process and you can learn from and share information with them. Several state departments of correction have already earned reputations for their technological innovation. While their exact approaches and methods may not fit your situation, the lessons they learned and the process they went through to establish their own technology systems might be helpful as you develop yours. You can reach out directly to these peers, engage them at industry gatherings such as national meetings and conferences of the Correctional Education Association and the American Correctional Association, as well as at regional meetings of the Correctional Education Association. The departments of corrections of Colorado, Louisiana, Maine, and Wisconsin were featured in RTI and the US Department of Education’s 2022 report “Building the Technology Ecosystem for Correctional Education.”[5] Recent programming at the Correctional Education Association’s annual conference highlighted recent work in this area ongoing in California, Kansas, Oregon, Ohio, and North Carolina. This list is not intended to be exhaustive—and we know other developments are already under way—but rather to demonstrate that departments of corrections throughout the country, and located in all major regions, are exploring and adopting technology for educational purposes in innovative ways. They have already learned many lessons the hard way: that means you don’t have to.
You can also reach out to third party organizations that perform research or technical assistance related to education in correctional settings. There are national nonprofit organizations that work closely in the field, such as American Institutes for Research (AIR), RTI international, Vera Institute for Justice, Jobs for the Future (JFF), and Ithaka S+R. There are also several university-based research organizations, such as the Research Collaborative on Higher Education in Prison at the University of Utah, and regional organizations, like the New England Board of Higher Education (NEBHE), that take on this work and have relevant knowledge and expertise. Many of these organizations will be willing to help share information and connect you to peers or colleagues who might have relevant experience. Some of them may also be able to provide ongoing technical assistance or consulting. We have listed several relevant organizations in the appendix Research, Technical Assistance, Advising and Professional Organizations.
Consider: How Targeted Technologies and Existing Technologies, Infrastructure, and Logistics Intersect
Our recent research on the role of technology in education in prison programming has emphasized that complex factors and hidden barriers complicate students’ ability to access and use technology effectively for educational purposes.[6] We’ve learned that there are often unforeseen or unexpected circumstances that can limit how, when, where, for how long, and in what conditions students are able to access and use. In fact, in our 2023 survey report examining the use of technology in higher education in prison programs, the majority of respondents who indicated that their students had access to technology for educational purposes also indicated that they did not have adequate access to that technology to sufficiently complete their coursework.[7] How instruction is delivered, what technology coursework can be completed on, what features and programs are available on that technology, what learning environments education and coursework occur in, and how long students can use educational technology in environments conducive to learning can all impact the effectiveness of technology implementation. For this reason, it is important to understand how existing technology devices and systems, the physical environment, movement procedures and patterns, and instructional methods and offerings all impact one another.
Our colleagues at JSTOR Labs developed this visual guide to help you think through some of the different considerations and constraints that arise with different instructional modalities and technology frameworks.
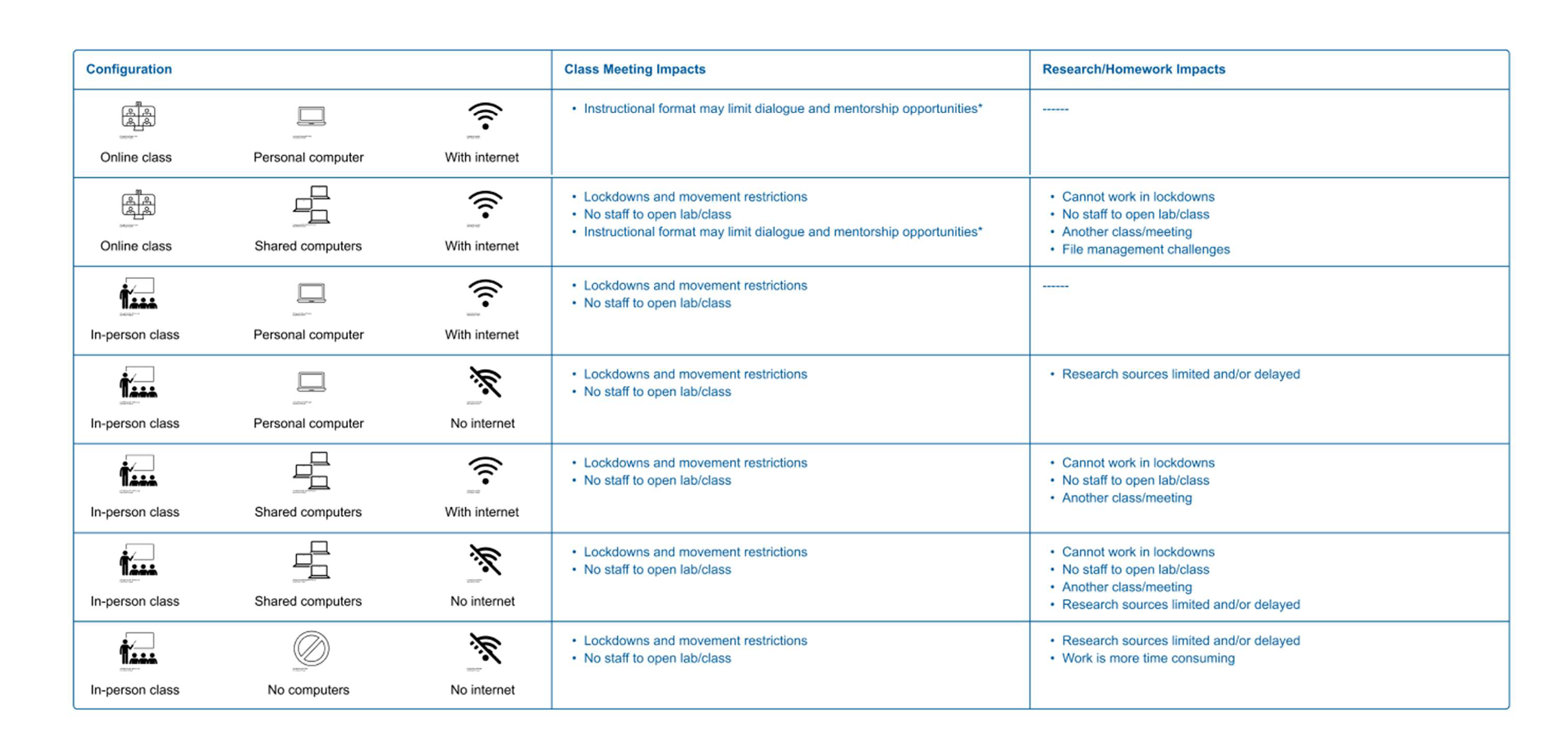 |
| Graphic by Nechelle Calhoun, Grace Cope, and Jessica Pokharel |
Below, we’ve developed some examples inspired by information we gathered through conversations with leaders in the field to help you think through other structural issues or unforeseen barriers to access, use, or conditions conducive to learning.
Example 1: Excellent Technology, Logistical Limitations
Instruction occurs entirely in person, but a department of corrections has acquired a set of brand-new laptops and contracted an outside organization to provide secure wireless services in all their facilities so that students can read course materials, conduct research, message instructors and campus service providers, and complete coursework in their residences.
During the installation and implementation process, it becomes clear that there are three unforeseen issues: (1) the physical structure of several facilities in the state has limited the effectiveness of wireless networks; (2) geographical concerns mean that one institution physically cannot be connected to broadband access by any existing providers in the state; and (3) device battery life is not as long as anticipated and effective use will require running new electrical to each individual unit so that devices can charge while students complete coursework in their residence.
In this case, while the technology acquired and the implementation plan have the potential to increase educational equity and digital literacy, logistical challenges that were overlooked in the initial planning have created site-based inequities in how technology is rolled out and where it can be used.
Example 2: A Robust Technology Ecosystem with Large Gaps between Frameworks
An institution already has a robust educational technology framework for secondary education, using a combination of tablets with secure 5G connection to course readings and approved, secure research databases, as well as access to shared computer labs. They work with a college partner to increase postsecondary education offerings, and the college agrees to fund the purchase of additional tablets for its students.
During implementation it becomes clear, however, that the tablets are not compatible with the college’s campus learning management system and students cannot access course materials or course readings on the tablets. And, while students can work on and type assignments on the tablets they have no way of transferring their work to the desktop computers in computer labs to edit, revise, or print them.
Example 3: Excellent Technology, Unforeseen Limitations
Instruction occurs in person at an institution with a long-standing postsecondary education in prison program. Recent technology expansions have allowed the facility to purchase laptop computers for short-term loans in a library and study space. Students have robust access to this space on evenings and weekends and have been spending several hours per week discussing assignments, writing papers, completing assignments, and accessing research materials.
Staffing issues force the institution to close the library and study space on evenings and weekends, meaning students can no longer use the laptops to study, work on assignments, research, or write papers. Policy dictates that no outside papers can be brought into the facility, so faculty cannot print and bring assigned readings or course assignments for students. To further complicate the situation, a lockdown cancels class for two weeks.
Example 4: Structural Decisions, Individual Impacts
A department of corrections audits who has been able to access and attend postsecondary education in prison programming and notices several previously unidentified barriers: some mandatory counseling programming and daily prescription pickup times conflict with class times. Classes are also only offered in a third-floor classroom and there are no other educational spaces available, due to spatial limitations and other state-mandated programming. Without intending to, these logistical issues have kept those individuals in counseling, those who need daily prescription medications, and those who have limited mobility from participating in postsecondary educational offerings.
Lessons From These Examples
These examples emphasize just how crucial communication, collaboration, and planning are to ensuring quality access and use of technology in the long-term.[8] Departments of corrections, individual facilities, and college partners need to understand how their decisions about technology intersect and can inadvertently limit the success of their students.
Certainly there are other scenarios that we can think through: scenarios where technology is used or abused in unexpected ways that break rules and procedures, scenarios where programmatic and logistical considerations limit access to education or educational technology in unforeseen ways, scenarios where technology becomes too dated to be compatible with current industry standard software, or where network access is a required component for the verification of a license to operate a given piece of software. To paraphrase a sentiment expressed by several leaders we spoke with: Things will go wrong, security breaches will happen, and there will be disruptions and problems. The key, according to those we spoke with, is to communicate, coordinate, and have procedures and plans in place to deal with issues without punishing or disrupting education writ large. You might call this a student-centered, security-informed, preparedness mindset. That is: you center the needs and experiences of students while supporting the achievement of educational objectives, you ensure that the approach is grounded in the security needs of relevant institutions and systems, and you establish and regularly review procedures for possible problems.
Phase Three: Preparation, Training, Pilot, and Beyond
Once you’ve planned and prepared, found funding, and acquired your target technology, it might be tempting to launch your new technology and iron out the wrinkles as they develop. Instead, we suggest building in one additional layer of preparation and training intended to explore unforeseen technical, policy, or procedural issues and to actively ensure that the various stakeholders are informed, invested, and prepared.
Consider: Who Needs to be Trained and Educated?
You’ve already worked to identify all of the relevant stakeholders, collaborators, and potential partners that are needed for successful technology implementation. Return to your map of stakeholders and consider:
- What does each group need to know about the technology acquired?
- What technical specifications or limitations might different groups or individuals need to be aware of?
- Who needs to be trained on how to secure it?
- Who needs to be trained on how to operate it?
- How can you ensure that instructors are prepared to incorporate the technology into their pedagogy?
- How can you ensure that students are prepared to use it?
- What policies and procedures outlining how, when, and where it can be used do different groups need to know about?
- What procedures are in place in the event of a breach or an abuse of technology?
- How will different groups be notified and what measures are in place to limit educational impacts?
- Who needs to be educated on or informed about the potential impacts or benefits of using this technology?
- Is it clear to security and operations, IT, instructors, and college partners why it is being implemented, how it should be used, and what objectives you are trying to achieve?
- Did any of those objectives or intended outcomes change between the time that you planned them initially and now that you are preparing to implement?
Exercise: Can you break it? Can we fix it? Testing Technologies, Policies, and Procedures Together
One novel way that we heard about to increase buy-in and to provide training on new technology systems was to build in time to ask different stakeholders to try to break, misuse, or abuse the new technology as a preparedness strategy. Such an approach may already be familiar to IT and security and operations teams; however, there is a benefit to involving a wider variety of stakeholders in the process. If you treat this as a diagnostic exercise to test the technology’s security and safety, its educational functionality, and the effectiveness of drafted policies and procedures, it can increase stakeholder buy-in and develop preparedness-informed procedures to technology breaches or unforeseen issues. Reinforce, though, that in addition to securing systems and limiting threats, you also want to ensure that education is not disrupted and that as few students and/or classes are impacted as possible. These twin goals of securing systems and ensuring educational access and the support of educational success can serve to bring security-centered and student education-centered mindsets into alignment.
This is also an opportunity to reconvene a variation of the group that you worked with in the exercise: Considering Constraints and Supports, Generating Solutions. We’ve provided brief directions to inspire two different versions of this exercise: one where you all work together as a team to test systems and the other where you spend more time robustly simulating use. Either of these activities can be adapted to fit a specific phase of technology implementation and can be treated as an internal meeting or workshop, an internal retreat, or a recurring activity.
Testing Systems
Directions: Begin by setting your intention together: the goal of this activity will be to look for weak points, gaps, or unexpected consequences in the technology you’ve established and the policies and procedures you’ve developed to govern and structure it. What haven’t you planned for that can go wrong? What have you planned that might have unexpected consequences?
Make sure that you have the technology to be tested ready at hand. Include any peripheral technology students may be able to use, as well—such as keyboards, headsets, computer mice etc. Distribute it to those in attendance as you provide the directions for Test 1.
Test 1: Normal Use
First, have the group test the technology in ways that they think students will need to use it: open applications, attempt to type papers, search for research resources, etc. Have the group explore, practice, and sample the technology as intended. Try to do things that users might need to do, some possible questions to consider:
- Can you open two programs simultaneously?
- Can you copy-paste or cut-paste from one program to another?
- Can you adjust font size or zoom?
- How do you scroll?
- How do you unlock the device?
- Are there any complications to this you might need to plan for?
- Are there accessibility considerations around unlocking the device you might need to be prepared to accommodate?
- I.e., if someone blind or with low vision is going to operate the device, can they see touchpads or line up facial recognition cameras to unlock?
- If someone with fine motor issues is using the device, is it stable? Can they unlock it? Can they select programs and features easily or is there a peripheral that can help them? etc.
- Can you use accessibility features like text-to-voice or voice-to-text?
- Can you navigate the programs and find how to do things like message an instructor or submit an assignment? (if either of these are applicable)
After you complete this activity, debrief as a group: what was easier than expected? What was harder? What might different stakeholder groups need help understanding or doing? Are there limitations that you didn’t anticipate? Will those issues impact the educational objectives you set?
Take notes on issues and, if needed, brainstorm solutions together.
Then prepare for Test 2.
Test 2: Break Rules and Systems to Fix Them
Now, you will have the group test the technology to see how students might use it in unanticipated or unsanctioned ways. The goal here is to do things that might break rules, damage, or upset systems, or get around security protections and protocols. This is not just a security exercise, though, we are looking for surprises, accidents, and mishaps as well.
Try to do things that users might want to do, do as a shortcut, or might do without, some possible questions to consider:
- What happens if you open all of the programs simultaneously?
- Can you change message recipients manually or reach external parties?
- Can modules or pages link externally?
- What happens if they do?
- Can someone with coding or systems knowledge get into the backend?
- Can the settings be manipulated in unexpected ways?
- If you can download or access readings, assignments, or other media, what happens if you download many things at once? What happens if you fill up the device memory?
- Can other people access or use the device?
- What fail safes or protocols are in place if they do?
Use your domain-specific knowledge to add to these questions.
When the group has completed the activity, discuss and debrief as a group: what problems did you notice? Do you have policies in place to deal with them? Are there any additional actions or practices that need to be planned for?
Simulating Use
This exercise will require a considerable investment of time. It can be planned as a day-long activity for the whole stakeholder group or broken apart and chunked into a series of discrete activities to be carried out over a longer period of time by smaller groups. While potentially beneficial for revealing how procedures, learning environments, and technologies might interact, this process can be time consuming and potentially disruptive.
In addition to testing the technical considerations and potential usability of the technology, simulating use conditions may allow us to discover if there are other procedural, logistical, or infrastructure issues we have not previously identified. Similar results can be achieved with a structured, limited pilot launch for a select group. There are, however, ethical concerns around selection and informed consent for such an activity which should be reckoned with well in advance.
Directions: The goal of this activity is to simulate actual use conditions. This will allow us to understand how use of the technology intersects with the infrastructure of a given facility, and procedures and protocols around movement and programming.
We will try to access and use the technology at the same time and in the same locations as future users will. The best way to do this will be to have an individual or small team simulate use throughout the day. Be sure to account for all the real-world conditions that a student-user will encounter, such as:
- Movement to and from locations where technology can be accessed, used, or charged.
- Technology use in all of the potential spaces where it may occur—libraries, study spaces, multipurpose rooms, residences, recreational areas or yards, workshops, etc.
- Technology use for periods of time, and ideally in the volume of traffic, that student-users might use technology.
- In these conditions, perform the Test 1 and Test 2 from the exercise above.
Conclusion: This is Only a Beginning
This playbook has offered a set of tools, exercises, and considerations to help you navigate initial planning to incorporate new technologies for educational purposes in a correctional setting. While expansive, it is not exhaustive. There are more considerations, more complications, and more nuance in this process, and no general guide can encapsulate the complexity and diversity of situations that individual departments of corrections, correctional institutions, and education in prison programs might be faced with.
Instead, we have tried to provide you with knowledge and information that might make the process or its planning less daunting. We suggest that you repeat the preliminary exercises in Gauging Where You Are, Considering Where You Want to Get on an annual basis to reassess how you are supporting educational goals, achieving and refreshing educational objectives to achieve in support of those goals, and collaborating with stakeholders.
We hope that this playbook has been useful, that it has offered some strategies and approaches that will make it easier to incorporate new education technology to improve educational outcomes, educational equity, and student educational experiences.
Appendix: Relevant Resources
Funding Sources for Implementing or Expanding Education Technology
National Telecommunications and Information Administration (NTIA) Digital Equity Act Grants
One of the largest sources of funding for programs, institutions, and agencies looking to expand educational technology offerings in prison has been funding available through the Digital Equity Act, which has several grant programs designed to expand broadband internet access and digital equity for underserved populations, including incarcerated individuals. Securing this funding, however, may require coordination and collaboration with other state agencies or partners, and the final deadline for states to submit proposals has passed. You can check your state’s grant proposals, which are publicly available, at the NTIA’s website.[9]
Carl D. Perkins Career and Technical Education Act Funding
Title I of the Carl D. Perkins Career and Technical Education Act provides state-based funds to advance career and technical education. A portion of overall funding is allocated to each state annually, though there are stipulations about how it can be spent and what data or information must be reported. Many states leave a portion of their Perkins funding unspent each year and this can be a renewable source of funding to help develop or maintain technology inside.
Workforce Innovation Opportunity Act (WIOA) Funding
The Workforce Innovation Opportunity Act provides funding to states on four-year plans designed to strategically align their core workforce development programs to help meet the needs of both employers and those seeking employment. Securing this funding will again require coordination and collaboration across state agencies and should be aimed specifically at developing the workforce. Like Perkins funding, state appropriations of WIOA funds frequently go underspent.
Direct Appeals to Legislators and Government Agencies and Offices
Direct appeals to governors or legislatures are an avenue of potential funding. Partnering with other state agencies—such as education departments, departments of labor or commerce, offices of probation and parole—may provide a more compelling case for funding to implement technology that serves to improve or expand educational offerings, increase employment or workforce development, and improve reentry outcomes.
Grants from Philanthropic Organizations
There are a number of philanthropic organizations dedicated to increasing educational access and equity—several of which fund initiatives in the sphere of education in corrections. This guide was made possible through funding provided by one such organization, Ascendium Education Group. If you work with postsecondary educational partners, you may be able to come up with compelling grant proposals to philanthropic organizations that serve educational needs, increase access and equity for underserved or nontraditional student populations, improve accessibility, increase literacy or digital equity, and increase access to specific disciplines—such as the arts or science, technology, engineering, and mathematics (STEM).
Cost Sharing Models with Educational Partners
New sources of funding may not always be available or readily accessible. In such cases, it might be worthwhile to pursue arrangements to share costs or the responsibility of securing and maintaining technology with educational partners. There may be cases where such an arrangement serves an educational partner’s mission or supplements its enrollment in meaningful ways. The reintroduction of federal Pell Grant funding for learners who are incarcerated in July of 2023 may increase interest in enrolling students who are incarcerated. Current market dynamics in the postsecondary education sector are pushing educational institutions to seek new student populations, be sure that any educational partnerships you develop serve the best interests of your students and support your educational objectives.
Research, Technical Assistance, Advising and Professional Organizations
- The Alliance for Higher Education in Prisons
- American Correctional Association
- American Institutes for Research (AIR)
- Correctional Education Association
- Ithaka S+R
- Jobs for the Future (JFF)
- JSTOR
- The New England Board of Higher Education (NEBHE)
- RTI International (RTI)
- Unlocked Labs
- Vera Institute of Justice
Helpful Research and Reporting
Hudson, Jordan, Laura Rasmussen Foster, Michelle C. Tolbert. “From Access to Use: Building an Equitable Student-Centered Educational Technology Ecosystem for Correctional Education.” RTI International. 3 November 2022. https://www.rti.org/insights/educational-technology-for-better-correctional-education-outcomes.
“Integrating Technology and Planning for Emergencies.” Vera Institute of Justice. Webinar recording. 2 July 2020. https://www.vera.org/research/integrating-technology-and-planning-for-emergencies.
Jones, Ben. “Navigating the Approval Process for Prison Education Program Technology.” Jobs for the Future. February 2024. https://info.jff.org/normalizingeducation/prison-education-program-technology.
–. “Pell is not enough: Exploring the experience of participants in Second Chance Pell.” The University of Utah. Collaborative for Higher Education Research and Policy. https://cherp.utah.edu/projects/pell_is_not_enough.php.
Note: Briefs 1, 4, and 9 are particularly relevant to considerations of technology in higher education in prison programming.
Pokornowski, Ess. “Technology in Higher Education in Prison Programs: A Report on Survey Findings.” Ithaka S+R. 7 September 2023. https://doi.org/10.18665/sr.319583.
–. “Resources.” The Resource Community for Higher Education in Prison. Accessed 25 September 2024. https://rchep.org/resources.
Note: The Resource Community for Higher Education in Prison features relevant information from a variety of sources and media and is searchable by topic. Much of the publicly available research and technical assistance information on technology in education in prison settings can be found there by searching “technology.”
Tolbert, Michelle, Sandra Staklis, Mihaela Henderson, Nicole Reddig. “Ready for Pell Evaluation.” RTI International. May 2024. https://dpjh8al9zd3a4.cloudfront.net/publication/ready-pell-evaluation/fulltext.pdf.
US Department of Education. Office of Career, Technical, and Adult Education. “Building the Technology Ecosystem for Correctional Education: Brief and Discussion Guide.” Prepared by Jordan Hudson, Laura Rasmussen Foster, Michelle Tolbert, and Brian Walsh. August 2022. https://lincs.ed.gov/sites/default/files/tech-ecosystem-correctional-ed.pdf.
West, Charlotte. “What happens when prison tech stops working.” College Inside. Open Campus. 11 May 2023. https://www.opencampusmedia.org/2023/05/11/what-happens-when-prison-tech-stops-working/.
–. “We asked people in prison about how they use technology.” College Inside. Open Campus. October 2023. https://www.opencampusmedia.org/wp-content/uploads/2023/11/EJ-Edits6_College-Inside-October-2023.pdf.
Coalitions and Consortia of Higher Education in Prison
These collectives may be able to provide state- or region-specific advising or assistance and can help build direct connections between corrections and higher education.
- Liberal Arts Consortium for Higher Education in Prison
- Big 10 Coalition for Higher Education in Prison
- Florida Coalition for Higher Education in Prison
- Georgia Coalition of Higher Education in Prison
- Illinois Coalition of Higher Education in Prison
- Iowa Consortium for Higher Education in Prisons
- Michigan Consortium for Higher Education in Prisons
- Mississippi Higher Education in Prison Consortium
- New York Consortium for Higher Education in Prison
- Oregon Consortium of Higher Education in Prison
- South Carolina Coalition of Higher Education in Prison
- Southern Higher Education in Prison Collective
- Tennessee Higher Education Initiative
Acknowledgements
Many thanks to Ascendium, who funded this and our previous work on technology in higher education in prison programming. Special thanks to all of the correctional and higher education in prison leaders, educators, alumni, and IT staff who made themselves available to us throughout the data collection process: your willingness to tell us about the field and the lessons you and your colleagues were learning made this work possible. Thanks to my colleagues at JSTOR Labs who were integral in the process of developing the playbook as well as those who provided design services on many of the visuals: Jessica Pokharel, Stacy Burnett, Nechelle Calhoun, and Grace Cope. Thanks also to Tommaso Bardelli, Kimberly Lutz, Juni Ahari, Laura Brown, Catharine Bond Hill.
Endnotes
- Michelle Hodara, Libbie Brey, Destiny McLennan, and Sam Riggs, “ECMC Foundation Basic Needs Initiative Evaluation Report 1: Sustaining Basic Needs Services at Postsecondary Institutions,” Education Northwest, January 2023, https://educationnorthwest.org/sites/default/files/pdf/ecme-bni-evaluation-report-508c.pdf; Joe Russo, Michael J.D. Vermeer, Dulani Woods, and Brian A. Jackson, “Leveraging Technology to Support Prisoner Reentry,” RAND, 3 May 2022, https://www.rand.org/pubs/research_reports/RRA108-12.html. ↑
- Pell Grants for Prison Education Programs; Determining the Amount of Federal Education Assistance Funds Received by Institutions of Higher Education (90/10); Change in Ownership and Change in Control, 87 FR 65426, codified at 34 CFR 600, 668, and 690, 2022. ↑
- Jordan Hudson, Laura Rasmussen Foster, Ess Pokornowski, and Kurtis Tanaka, “Aligning the Conversation on Technology Use for Education Programs in Prisons and Jails,” Ithaka S+R, 31 October 2023, https://sr.ithaka.org/blog/aligning-the-conversation-on-technology-use-for-education-programs-in-prisons-and-jails/. ↑
- Alex Humphreys, “Constraint-storming, Not Brainstorming,” JSTOR Labs, 14 October 2022, https://labs.jstor.org/blog/constraint-storming-not-brainstorming/. ↑
- US Department of Education. Office of Career, Technical, and Adult Education, “Building the Technology Ecosystem for Correctional Education: Brief and Discussion Guide,” prepared by Jordan Hudson, Laura Rasmussen Foster, Michelle Tolbert and Brian Walsh, August 2022, https://lincs.ed.gov/sites/default/files/tech-ecosystem-correctional-ed.pdf. ↑
- Ess Pokornowski, “Technology in Higher Education in Prison Programs: A Report on Survey Findings,” Ithaka S+R, 7 September 2023, https://doi.org/10.18665/sr.319583;Jordan Hudson, Laura Rasmussen Foster, Ess Pokornowski, and Kurtis Tanaka, “Aligning the Conversation on Technology Use for Education Programs in Prisons and Jails,” Ithaka S+R, 31 October 2023; Tammy Ortiz, Sindy Lopez, and Ess Pokornowski, “Uneven Terrain: Learning Spaces in Higher Education in Prison,” Ithaka S+R, 7 October 2024. https://doi.org/10.18665/sr.321385. ↑
- See Figure 10: Do students have sufficient access to [desktop computers, laptops, tablets] to adequately complete coursework and assignments? in Pokornowski, “Technology in Higher Education in Prison Programs.” ↑
- In the case of postsecondary education programs drawing on federal Pell Grant funding, it is important to note that if education is disrupted and students cannot complete a semester, colleges are legally obliged to return grant funding and students cannot recover the term of Pell eligibility expended for the incomplete semester. ↑
- “Public Notice Posting of State and Territory BEAD and Digital Equity Plan, Initial Proposals, and Challenge Process Portals,” NTIA, Broadband USA, https://broadbandusa.ntia.gov/public-notice-posting-state-and-territory-bead-digital-equity. ↑